Take a look, and let me know what you think.
Friday, October 7, 2011
App Review: Trello for Project Management
Take a look, and let me know what you think.
Saturday, March 28, 2009
My Speedtile Shared Bookmarks
 I often get asked by my students about my favorite search engines, my favorite help sites, my favorite e-commerce information pages etc. - so, I thought this might be an opportunity to share my bookmarks with not only my students – but the world at large.
I often get asked by my students about my favorite search engines, my favorite help sites, my favorite e-commerce information pages etc. - so, I thought this might be an opportunity to share my bookmarks with not only my students – but the world at large.In searching for a good bookmarking service, I came across Speedtile.net – a visual bookmarking service which is just freaking awesome! and with its firefox plugin, all I need to do is right click the web page I want to bookmark, and its done (as long as I’m logged into my speedtile account). For those who haven’t used Speedtile before, I really encourage you to give it a try. You can organize your bookmarks in different categories (structured as tabs on the website) and decide which specific ones you’d like to share by simply dragging and dropping the snapshots into the shared tab.In your profile, you can also select a label which will be used to personalize the URL for your shared bookmarks. In my case, I created two accounts – one to share my search engine and help sites bookmarks, and the other to share my ecommerce bookmarks.
The respective URLs are as follows:
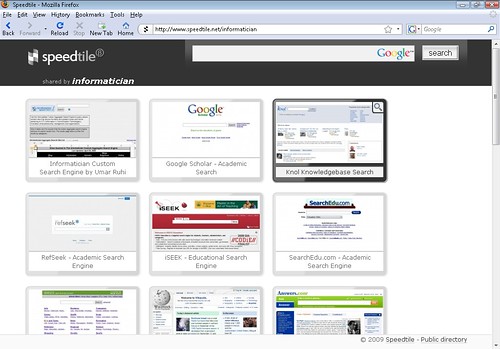
The other good thing about speedtile is their fast and easy sign-up/registration process. I can’t remember the last time I gave out information only relevant to the service I’m signing up for. The registration form only asks for an email address and a password ! yeap… that’s it – check it out for yourself.
So check out speedtile, and check out my shared bookmarks at the URLs above. Let me know if I missed anything big from these bookmarks. I suspect I’ll be updating these on a regular basis.
Tuesday, March 24, 2009
CanPages brings Street View to Canada - Move over Google!
 Like many other people I know, I’ve been waiting anxiously for Google Street View to be launched in Canada. It seems that Google has had some difficulty in complying with the federal privacy legislation in Canada, and that’s the primary reason why the service hasn’t made it here just yet.
Like many other people I know, I’ve been waiting anxiously for Google Street View to be launched in Canada. It seems that Google has had some difficulty in complying with the federal privacy legislation in Canada, and that’s the primary reason why the service hasn’t made it here just yet.The main issue here is the high-resolution personal images and other identifiable information (e.g. car license plates) that have sometimes accompanied Google’s street view in the other countries where it was launched previously (including U.S., U.K. and France). Collecting personal images without the explicit consent of the people in those images is a prohibited practice under Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA).
So while Google is getting ready to start filming Canadian cities, Canadians have another alternative to check out. We now have our own Street View equivalent in some cities - thanks to the partnership between the British Columbia-based yellow pages directory service provider CanPages.ca, and San Francisco-based MapJack.
By my own initial assessment, the street view service offered by CanPages is a strong contender for Google Street View. In fact, I’ve seen features in Canpages.ca that I haven’t seen in Google Street View – e.g. high resolution full screen mode, pedestrian pathway views, image configuration, and did I mention pedestrian pathway views. The virtual 360 degree panning works pretty well too.
The service has been launched in Vancouver and some other parts of British Columbia, perhaps rightly so, given the timeline for the Winter Olympics in 2010. I suspect the service will be a hit with the tourists!
To check out the various features myself, I decided to virtual walk the part of the city that I’m most familiar with from my last visit to Vancouver. Since the CanPages.ca service is primarily a yellow pages service, I had to supply a business name or a landmark to get started, and I searched for the Sheraton Wall Centre Hotel in Vancouver where I’ve stayed previously. Once the listing was displayed, I clicked on the Street View option and panned 180 degrees to get to the front view of the hotel building (see screenshot below).
Notice the various visual aids such as zoom, pan, and full-screen options, as well as the inline blue dots where more views of the street are available. Also, a small cartoon figure (let's call him virtual voyager) appears on the street map for orientation and reference (pretty cool!).
Here’s a screenshot of the full-screen view (size reduced for posting here of course). It truly allows users to immerse themselves into the cityscape.

In terms of its business model, the new Street View offering is aligned with CanPages’ yellow pages service, as it provides advertisers – especially local businesses an innovative means of reaching the website's visitors. Specifically, when a user clicks on a storefront in Street View, he/she will get to see a local profile of the business, and possibly other relevant links to video advertisements, website URL, and general information such as hours of operation or restaurant menus in the case of food service locations.
Overall, I think it’s a sound business offering as it comprises enough originality to spark end-user interest and also presents long-term functional value to the consumer.
Friday, March 13, 2009
Free Google Mobile Phone Services
 I recently offered a graduate seminar course on Mobile Commerce at the University of Ottawa, and it was pretty surprising to see how many mobile end-users still don’t use third party applications and services that exist outside the realm of their service provider’s portfolio. This end-user behavior is highly representative of the Canadian mobile services landscape where our industry structure is highly vertical and the service structure is highly integrated. In Canada, the operators exercise a lot of control over the entire mobile value chain. Companies like Rogers, Telus, and Bell provide services including voice, messaging, internet, and email functions as prepackaged bundles. The customers have little choice in selecting the specific modules that they might be more interested in. Furthermore, the mobile portals on handhelds are usually preconfigured to link to the service provider’s solutions, and do not offer other choices – even free service choices. Many students in my class hadn’t even heard of the following google services that are offered for free (barring the operator’s data transmission charages):
I recently offered a graduate seminar course on Mobile Commerce at the University of Ottawa, and it was pretty surprising to see how many mobile end-users still don’t use third party applications and services that exist outside the realm of their service provider’s portfolio. This end-user behavior is highly representative of the Canadian mobile services landscape where our industry structure is highly vertical and the service structure is highly integrated. In Canada, the operators exercise a lot of control over the entire mobile value chain. Companies like Rogers, Telus, and Bell provide services including voice, messaging, internet, and email functions as prepackaged bundles. The customers have little choice in selecting the specific modules that they might be more interested in. Furthermore, the mobile portals on handhelds are usually preconfigured to link to the service provider’s solutions, and do not offer other choices – even free service choices. Many students in my class hadn’t even heard of the following google services that are offered for free (barring the operator’s data transmission charages):Google 411 (1-800-GOOG-411) Website Link

Google’s voice local search service for local businesses uses speech recognition technology to allow users to query for and connect to businesses. Users can search for businesses by name or category (which is a definite plus in comparison with the traditional 411 service offered by operators). The service then generates a list of businesses that match the user’s query, and allows the users to select an entry from the list. Following the selection, the user can either directly get connected to the business or ask for a text message to be sent with the relevant business details. For users with internet access and google maps, the service also accepts the “map it” voice command to show a map of the business neighborhood.
So not only is the service free to use, but it has advanced features not available through the directory assistance service offered by many operators. For Canadian users, until we get something like TellMe.com, this is the next best thing – store 1-800-GOOG-411 (1-800-466-4411) in your contact list and start using it !
Google SMS (46645) Website Link

This is Google’s fast information response service (SMS number 46645), and it lets users send quick queries to Google via SMS and get back responses. Rather than using your data quota in accessing different search engines or websites, the service allows users to quickly get back the information they’re looking for. The service supports specific types of queries such as weather reports, movies, stock quotes, directions, and local businesses by name or category. See this page for examples of queries. To get started, you can try some queries on the online emulator provided here and get familiar with the results. Again, it's not just a free service, but something that’s much easier to use in comparison to its alternatives (e.g. browsing the internet on your handheld to get the information) – store 46645 in your contact list and start using it for SMS queries.
Do you know of any other useful free mobile phone services? If so, leave your comment below, or send me a note.
Tuesday, February 3, 2009
Book Review - Enterprise 2.0 by Niall Cook (2008)

Recently I had the opportunity to write a book review on Academici for a new book titled "Enterprise 2.0". I thought I just as well post the review here too. The original review appears here: http://www.academici.com/blog.aspx?bid=5676
CITATION
Cook, N. (2008). Enterprise 2.0: How Social Software Will Change the Future of Work. Hampshire, England: Gower Publishing Limited.
DETAILS
Author: Niall Cook
Title: Enterprise 2.0: How Social Software Will Change the Future of Work
Publisher: Gower Publishing
Publication Date: 2008
ISBN: 978-0566088001
Price: (US) $89.95
LINKS
REVIEW
Constructive applications of social software within a business context have garnered a lot of recent interest from practitioners as well as the research community. After an influential foray on the Internet, Web 2.0 technologies are being touted by many to bring significant benefits to organizations through their ability to facilitate agile collaboration and efficient information sharing across business functional areas.
Niall Cook’s Enterprise 2.0 is an opportunely timed book that provides a managerial overview of Web 2.0 technologies for businesses. At a time when organizations are starting to get serious about their Web 2.0 technology investments, Enterprise 2.0 can prove to be a useful and practical primer for getting a grasp on Web 2.0 technologies for the workplace. As social software applications such as blogs, wikis, social networking, collaborative tagging, social bookmarking and microblogging start to move beyond the pilot stages of implementation in many organizations, executives, managers, process owners, as well as technologists will need to know how to effectively implement and institutionalize these applications within the organization.
Recent industry trends also show that organizations that have been experimenting with social software technologies will most likely be looking at deploying them in the form of an integrated solution comprising of a multitude of tools and applications. This shift in the market from individual technologies to integrated solutions, accompanied with the aspiration for enterprise-wide deployment will require qualified strategy formulation, careful planning, and capable project execution. Enterprise 2.0 delves into sufficient details about each of these aspects of deployment and use of social enterprise software within the organization.
The discussion throughout the book is tied together with the 4 Cs framework (Communication, Cooperation, Collaboration, Connection) which the author initially introduces as a classification scheme for social software. Progressing through the book, it becomes clear though, that the 4Cs framework is not only a valuable analysis framework for conceptually making sense of the types of social software applications and their uses, but also for performing an assessment of the organization’s technology requirements and translating them into functional specifications. The examples and use cases provided with the 4Cs framework foster a better understanding of the potential gains and improvements that can be achieved through enterprise social software. The book’s managerial style narration and its references to various real world case studies make it easy for the discerning executive to comprehend the business case for investing in key social software tools and applications.
After helping the reader gain a sense of the business case for enterprise social software, the author moves on to suggesting a methodology for implementation and institutionalization of these technologies. Significant emphasis is placed on the adoption of technologies and overcoming resistance from staff. Toward this, the author aligns himself with the notion of accentuating user value over network value – i.e. drawing attention to the benefits of social software applications to individual users before talking about their benefits to the business. This can prove to be especially useful in getting the passive or less active users on board with the program. Beyond advice, the author proposes specific tactics to encourage user participation and speedier organization wide adoption by offering guidelines that can be adapted for different social and political cultures.
The last part of the book is dedicated to a review of the literature on enterprise social software. As an invaluable resource for the academic readers, this section provides a current review of terms and definitions related to the subject, as well as a summary of the conceptual treatise of enterprise social software found in seminal works.
To conclude this review, as organizations embark on projects to implement comprehensive enterprise software solutions that integrate multiple technologies into unified platforms, they need to rely on guidelines and recommendations from prior research, practitioner experiences, expert opinions, and lessons learned by others in their projects. Enterprise 2.0 provides a useful synthesis of these resources in the form of a discourse that will appeal to both the industry and the academic communities.
Monday, December 29, 2008
Exploring Mashups – Part III: A Geo-coded Mashup using Dapper, Yahoo Pipes & Google Maps
Sunday, December 14, 2008
Playing with Mashups - Part II : Integrating Dapper with Popfly
This blog post follows from a previous one where I experimented and mulled over the functions provided by the content mapping and mashup functionality provided by Dapper. In my first trial run, I created a mashup for an online discussion forum in which I participate on a regular basis. The mashup was pretty simple – yet, it was the result of composing several dapps together in an iterative manner using a variety of information output formats. In this post, I am summarizing how I was able to take the final dapp that was created in part 1, and use it as an input to Microsoft’s Popfly mashup creator.
The data flow schematic and the popfly screenshot below reveal the configuration between the dapp and the popfly mashup. What’s happening here is that the dapp is used to output an RSS feed which is then captured by the RSS block in popfly. The specific items from the RSS feed are then rendered as a table.
- Dapper gathers feeds from the online forum and combines those feeds with last posters avatars into a data object;
- Popfly acquires the new data object and displays the data
Wednesday, December 10, 2008
Playing with Mashups - Part I : Using Dapper for Content Mapping
This is the first blog post in what I plan to be a series of posts to share my experiences with various mashup building applications online.
Over the last couple of days, I’ve been playing with the data mapping and mashup functionality provided by Dapper. Overall, my experience has been rather pleasant, and I would definitely suggest the service to someone who’s just getting started with mashups. It should be noted however, that on the outset, Dapper is more of a data mapping service than a mashup. The main features and functions of Dapper allow the end-user to extract pieces of information from websites and label and organize the information in a logical structure. The resulting information structure can then be output in various formats including XML, HTML, and RSS feeds, or it can be rendered in specific applications such as a Google Gadget or a Flash Widget. It’s pretty cool when you try all the available output options for the first time.
So to test out the basic functionality of Dapper, I set out on a simple task to query the Google Scholar search engine and fetch the list of my research publications. I thought this might result in something I would want to use in the future… and I was right. Other than the fact that Google Scholar still does not index many academic repositories and hence, the results are not comprehensive, I did get some results which I was able to formulate into a dapp. The resulting dapp was then rendered as a flash widget (shown below).
Here is a summary of the procedure to get to the results as displayed in the flash widget above.
1. Login to Dapper
2. In the section titled, Get any content from the Web, click on create a new Dapp
3. Enter the Google Scholar URL pointing to the search results you want to extract from.
In my case, I used: http://scholar.google.ca/scholar?q=author:"Umar+Ruhi"&num=100&scoring=r
My name is specified in the author parameter. The num=100 parameter specifies the number of search results to show; and scoring=r specifies that I would like “r”(recent) articles to be listed first.
Under the form address bar, you can leave the format as Dapp XML.The output format can be customized later.
4. Once you see the google search results in Dapper’s virtual browser, you can select “Add to Basket”.
5. Ideally, at this point, it is recommended that you also give Dapper a couple of other similar pages (e.g. search results for other authors), so that Dapper can make some sense of the webpage structures. I didn’t really feel the need to do so in this case. If you want Dapper to just analyze the webpage structure of more pages, you can enter their URLs and “Add to Basket”. Once done, you can click on the Next Step button.
6. With the page(s) in the basket, you can start selecting areas of the page that you would like to save into your information structure for output. For example, I clicked on the titles of the search results which highlighted all the titles on the page. Sometimes, Dapper will select other non-related areas automatically, and you will need to manually de-select these by clicking the Clear link for the item(s) in the Preview selected content pane.
7. If you’re satisfied with the selection of information items, you can click on the Save Field button and provide a label for the field.
8. Steps 6 and 7 can be repeated to gather more information items from the webpage in the basket. With all the content fields identified, you can click on the Next Step button.
9. On the next screen, you will group the content fields and provide group name(s). These group names will be used to structure the resulting dapps. With all the groups specified, click on the Next Step button to proceed to the last screen.
10. On the last screen, you will be asked to save the dapp and provide a description. You will also have the option of making the dapp private, i.e. only you or someone who knows the exact address of the dapp or its output feeds will be able to access it. I use the private option for most of my dapps which I know have little utility for anyone else.
The input variables are meant to provide a mechanism for allowing an end-user to customize how the dapp is called. It is an optional feature, and you can click on the help link to learn more. Click Save when you’re done entering all the details of the dapp.
11. Now that the dapp is created, you will be presented with a variety of output options which you can play around with to see which option works best for you. As shown above, I selected the flash widget to present the results of my dapp.
That’s about it in terms of how the Google Scholar dapp was created. For everyone who’s interested in exploring Dapper, I also hope this mini-tutorial comes in handy for learning about other basic features of Dapper.
Friday, September 19, 2008
Security Authentication & Authorization: The Case of Sarah Palin's Email Account Breach
This case makes a rather interesting discussion piece for a course I teach on Internet Security… and reminds me of the many conversations I’ve had with security colleagues in the past when I was involved with the implementation and institutionalization of authentication credentials, access control procedures, authorization mechanisms, and single-sign-on (SSO) implementations.
The gist of the story about Sarah Palin’s Yahoo! email hacking is that the intruder gained access via the forgotten password mechanism on the Yahoo! webmail interface. By following the typical verification prompts and challenge questions, the intruder was able to reset the profile's password. All that was needed were just a few pieces of information that were easily acquired through Google searches and Wikipedia entries about the Alaska Governor. Overall, this was a case of knowledge-based security mechanism hack, and it is also a classic illustration of the importance of proper password management. It demonstrates how our common password habits can expose us to a rather simple security hack. That being said, the consequential impact of this simple hack can turn out to be something quite destructive such as the disclosure of confidential information.
Relevant details and a quick chronology of this incident are as follows:
- the person (lets call him Rubico) who hacked in to Sarah Palin’s Yahoo! account used “an anonymizer” service called CTunnel (http://www.CTunnel.com) to browse to the Yahoo! email service site.
- Rubico used Sarah Palin’s email address on the login screen and clicked on the "Forgot your ID or password?" link. He knew Palin’s correct email address from several online websites of government institutions, groups and committees that Palin had served on.
- Rubico was then prompted to either supply an alternative email address for resetting the password, or to choose the option to reset without access to a registered email account. To me, this option to bypass the alternative email mechanism is an obvious red flag. Rubico, as can be expected, chose the latter option.
- At this point, Rubico was asked to answer a "secret" security question. This so called knowledge-based authentication is supposed to add an additional layer of validation in a single-factor authentication scheme whereby the end-user has to provide something else he/she knows. In Palin’s case, her “secret” question was “Where did you meet your spouse?”, and Rubico had found the information to answer this question through public sources. Apparently, she had revealed in her TV interviews that she and her husband were high school sweethearts. So Rubico tried a couple of variations of the name of the local high school where she grew up and eventually got a hit on “Wasilla High”.
- Finally, the Yahoo! account profile verification prompts ask to verify the ZIP code and Country. Once again, for public figures such as Palin, this information is generally commonly available.
- Once Rubico entered the correct answer to that single “secret” question, and completed the profile verification prompts he was immediately allowed to change Palin’s password, and he promptly changed it to “popcorn”. At this point, if you’re like me, you’re probably wondering why Yahoo! didn’t make the password reset mechanism and the validation workflow a little more challenging.
- The only somewhat positive aspect of the validation workflow is its last step where the end-user is notified that his/her account is now "up to date", and that he/she will also receive an email on the alternative email account with a notification of the changes that were made to the account. This is probably how Palin would have discovered that her Yahoo! email account was compromised, but alas, that news was already out in the open through numerouschat channels and public discussion forums.
So, it’s pretty apparent in this situation that the authentication mechanism is only as strong as its weakest component, and the fact that there is an option to reset the password without ever having to leave the browser window is a critical issue in the validation workflow. Why not include an out-of-band multiple factor authentication component to authorize security related changes such as password resets? Why not use something similar to MyOpenID (http://www.myopenid.com) or Passpack (http://www.passpack.com) to complement or strengthen the current procedures?




